Speak the language of security with an SSL certificate. The little green lock lets visitors know that you’ll keep their data safe.
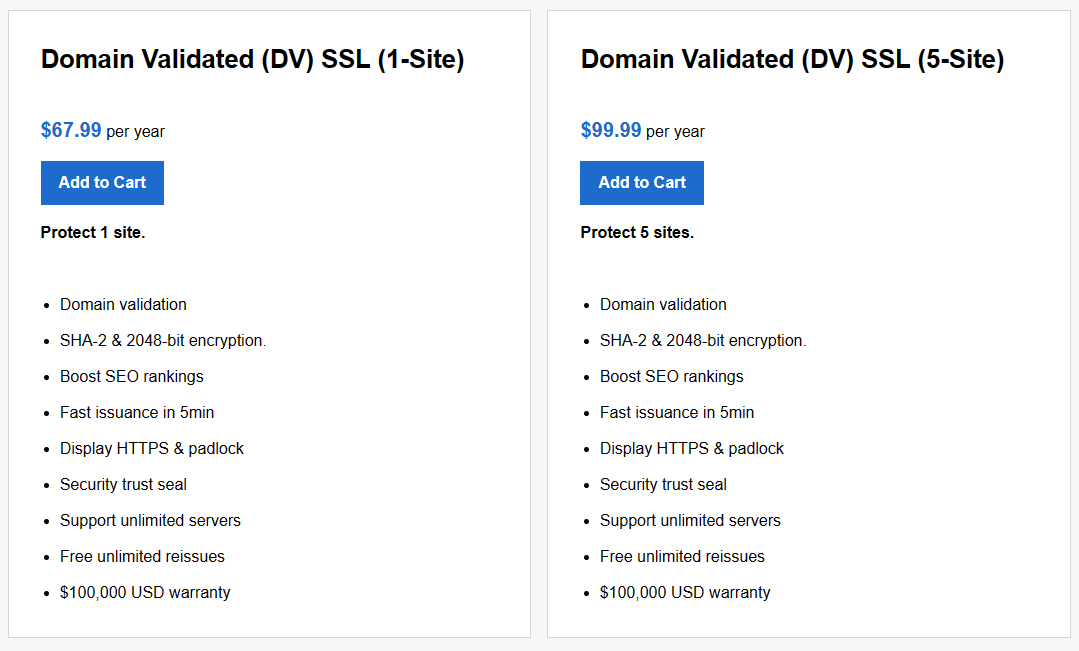
Domain Validated (DV) SSL
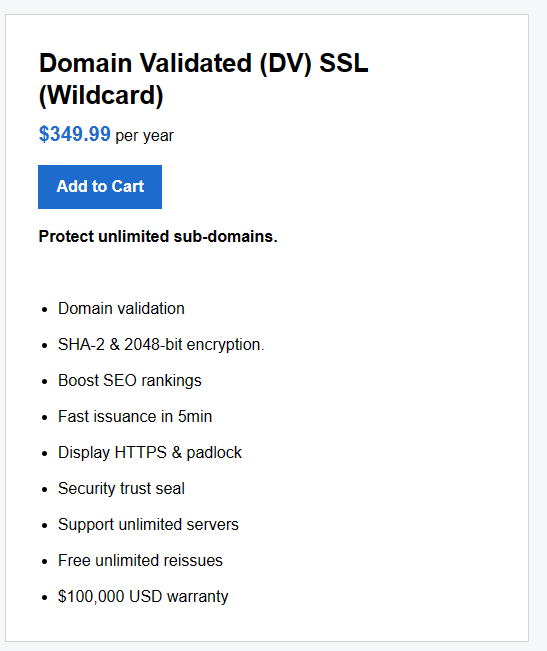
Domain Validated (DV) SSL (Wildcard)
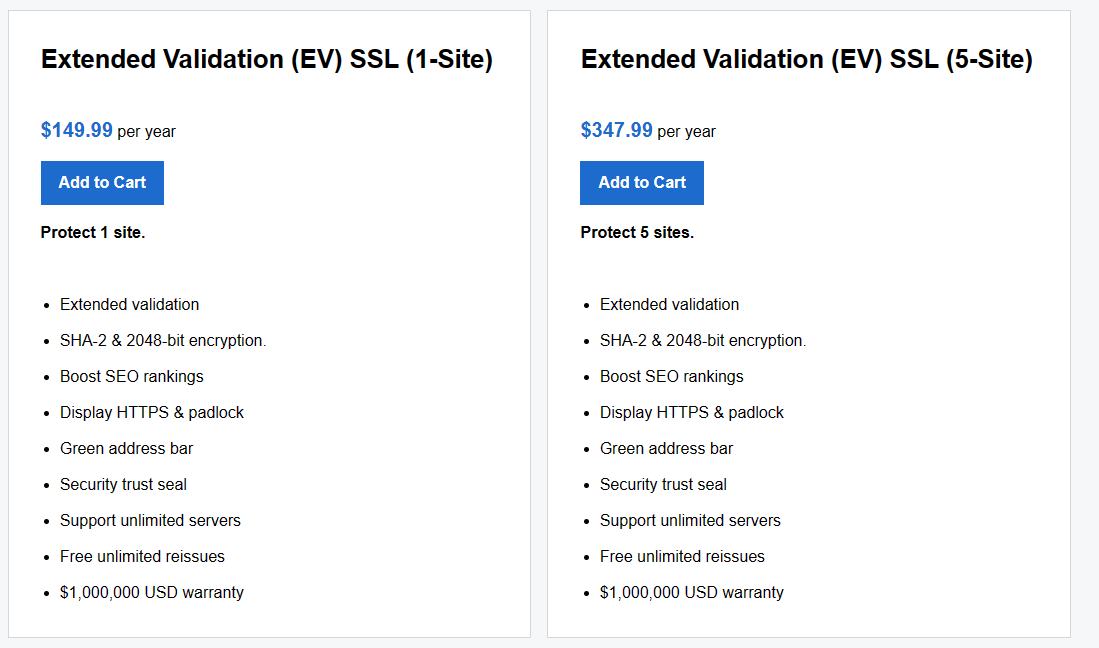
Extended Validation (EV) SSL
SSL stands for Secure Socket Layer. It might sound complex, but it’s really not. SSL Certificates validate your website’s identity, and encrypt the information visitors send to, or receive from, your site. This keeps thieves from spying on any exchange between you and your shoppers. When you have an SSL Certificate protecting your website, your customers can rest assured that the information they enter on any secured page is private and can’t be viewed by cyber crooks. PowerHoster makes it easy to install your certificate and secure your server.
How to Install Your SSL Certificate ?
- Request the SSL
Specify your domain name and the type of web server that’s hosting your site. - Verify your SSL
Then verify that you control the domain — verification depends on the type of certificate and web server. - Download your SSL
Download your primary and intermediate certificates from the SSL dashboard. - Redirect HTTP
Once installed, redirect your visitors to the secured (HTTPS) version of your site. Address which of these pertain to you. - Check Installation
Enter your URL into a browser. Look for the padlock icon before your URL, if it’s there, you’ve completed installation and your site is SSL secure.
What Makes our SSLs Better?
All SSL-protected sites display the https:// prefix in the URL address bar. Sites protected with a Premium EV SSL Certificate display a green browser bar to quickly assure visitors that the organization’s legal and physical existence was verified according to strict industry standards.
PowerHoster’s Premium EV SSL Certificate involves the most extensive vetting process. We verify the control of the domain and legitimacy of your company by validating the legal name, address, phone number and other business information. The process takes about 30 days, but we’ve got you covered during that time. EV SSL Certs come with a free Standard SSL to use during the vetting process, so you can keep your transactions secure while you wait.
What is Encryption?
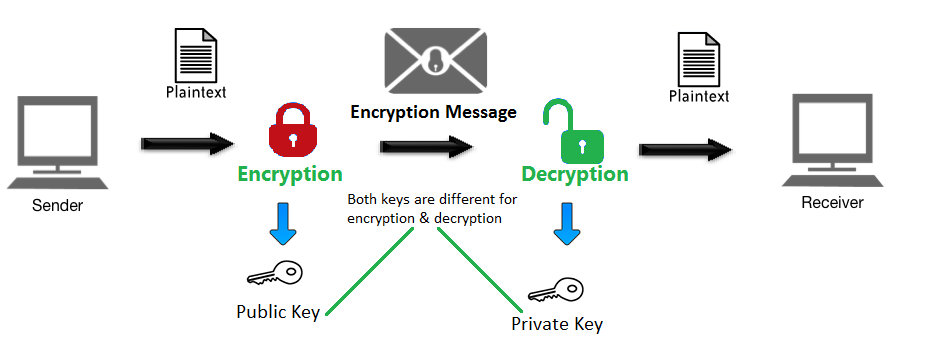
The encryption process in SSL/TLS (Secure Sockets Layer/Transport Layer Security) involves the use of cryptographic algorithms to secure the communication between a client (such as a web browser) and a server. The primary goal of SSL/TLS encryption is to ensure the confidentiality and integrity of data during transmission over the internet. Here’s a simplified explanation of how the encryption process works:
- Handshake:
- The SSL/TLS handshake is the initial phase where the client and server establish a secure connection. During this process, they agree on cryptographic parameters, exchange keying material, and authenticate each other.
- Key Exchange:
- The handshake includes a key exchange mechanism to establish a shared secret key between the client and server. This key is used for symmetric encryption, where the same key is used for both encryption and decryption.
- Symmetric Encryption:
- Once the shared secret key is established, both the client and server switch to symmetric encryption for the actual data transmission. Symmetric encryption is more efficient than asymmetric encryption for large amounts of data.
- The symmetric encryption algorithm (e.g., AES – Advanced Encryption Standard) and the shared key are used to encrypt and decrypt the data.
- Data Encryption:
- The data is divided into blocks, and each block is encrypted individually using the symmetric key. This ensures that even if an attacker intercepts the encrypted data, it is challenging to derive meaningful information without the key.
- The encrypted data is then transmitted over the network.
- Integrity Check:
- To ensure data integrity, a Message Authentication Code (MAC) or Hash-based Message Authentication Code (HMAC) is often used. This code is calculated using the shared secret key and is sent along with the encrypted data.
- Upon receiving the data, the recipient can verify the integrity by recalculating the MAC and comparing it to the received one. If they match, it indicates that the data has not been tampered with during transmission.
- Decryption:
- At the receiving end, the encrypted data is decrypted using the shared secret key. The symmetric encryption algorithm and the key are used to reverse the encryption process, turning the ciphertext back into plaintext.
- Session Termination:
- Once the secure communication session is complete, the SSL/TLS connection may be terminated. The symmetric key is discarded, and a new key will be established if a new session is initiated.
The use of encryption in SSL/TLS ensures that even if a malicious actor intercepts the transmitted data, it remains confidential and secure. The encryption process, combined with the authentication and key exchange mechanisms of the handshake, forms a robust system for securing data during communication over the internet.
The Benefits of Using SSL Certificates
- Safely accept credit cards on your website – Protect both customer and internal data. If you want to sell to a much larger audience, you need to give customers the payment options they prefer — AND you need an SSL to keep customers clicking through to checkout.
- Increase customer confidence – Most people look for the https:// prefix in their browser bar before submitting personal information like their name, credit card number and address to a website. An SSL is the only way to get this.
- Protect sensitive information – SSL Certificates protect your customers’ sensitive information by encrypting the data they send to you, then decrypting it once you’ve received it.
- Build customer trust and improve conversions – When your customers find your websites are safe, they will be come back to order again as a repeated customers and new customers.
- Encrypt browser-to-server and server-to-server communication – Your browser to server and server to browser communication will be encrypted. It will prevent some hackers to hack your websites and steal your website information.
- Increase security of your mobile and cloud apps – When your visitors are viewing your website by mobile, their mobile are safe and not easy to be hackered.
- the SSL agreement – When a visitor enters an SSL-protected website, your SSL certificate automatically creates a secure, encrypted connection with their browser. Your site is most secure when SSL is deployed on all pages and subdomains.
- The padlock icon appears – Once the connection is complete, a padlock icon and https prefix appear in the visitor’s browser bar to show visitors to your website they’re safe to browse, shop, email you, subscribe to your mailing list, etc. And if there was a Not Secure tag before, poof now it’s gone.
How does SSL Work ?
SSL, or Secure Sockets Layer, is a protocol that ensures the security of data transmitted over the internet. It has been succeeded by TLS (Transport Layer Security), but the term “SSL” is still commonly used to refer to both protocols.
Here’s a simplified explanation of how SSL/TLS works:
- Handshake:
- The process begins with a handshake between the client (e.g., your web browser) and the server (e.g., the website you’re connecting to).
- The client sends a “Hello” message to the server, indicating that it wants to establish a secure connection.
- The server responds with its own “Hello” message, including its SSL certificate.
- SSL Certificate:
- An SSL certificate is a digital certificate that authenticates the identity of the server (or sometimes the client). It contains the server’s public key, information about the certificate’s owner, and the digital signature of the certificate-issuing authority.
- The client checks the server’s certificate to verify its authenticity. If the certificate is valid, the client proceeds to the next step.
- Key Exchange:
- After verifying the certificate, the client and server engage in a key exchange to establish a shared secret key. This is typically done using asymmetric encryption, where the server’s public key is used to encrypt a shared secret, and only the server’s private key can decrypt it.
- This shared secret key will be used for symmetric encryption, which is more efficient for encrypting the actual data being transmitted.
- Symmetric Encryption:
- Once the shared secret key is established, both the client and server switch to symmetric encryption. This means they use the same key for both encryption and decryption.
- Symmetric encryption is faster than asymmetric encryption, making it suitable for encrypting large amounts of data.
- Data Transfer:
- With the secure connection established, data can now be transmitted between the client and server over the encrypted connection. This ensures that even if someone intercepts the data, they won’t be able to understand it without the shared secret key.
- Termination:
- When the secure connection is no longer needed, either the client or server (usually the client) can initiate the termination of the SSL/TLS connection.
The SSL/TLS protocol helps protect sensitive information, such as login credentials, credit card numbers, and other personal data, from unauthorized access during transmission over the internet. It provides a secure channel for communication between the client and server, preventing eavesdropping and tampering with the data.
How Many Unique Domains do You Want to Secure With HTTPS?
Do all of the sites have fully qualified domain names, or do you need to add a few subdomains on the fly?
- Single-domain SSLs cover one domain or subdomain. For example, you can secure www.coolexample.com. You can purchase single-domain SSL’s as Standard, Deluxe High Assurance (OV) certificates, or EV certificates.
- Wildcard SSLs cover multiple subdomains. For example, you can secure *.coolexample.com, which would cover shop.coolexample.com, www.coolexample.com, and any other subdomains. You can purchase Wildcard SSLs as Standard or OV certificates.
- Multiple Domain (UCC) SSLs can cover multiple subdomains, unique domain names, and websites. For example, you can secure www.coolexample.com, mail.coolexample.com, and www.awesomeexample.com. You can purchase UCC SSL’s as standard or EV certificates.Encrypted data is shared between the browser/server and the Web server. All information passing to and from your website is now scrambled by 2048-bit encryption that’s virtually unbreakable by hackers.
- EV UCC SSLs represent all secondary domains with the primary business name, so all sites should be related. A UCC site seal displays only the primary domain name as “Issued To,” and all secondary websites are listed in the certificate details.
Why Should You Buy SSL From PowerHoster ?
1.We empower entrepreneurs and their communities.
2. You’ll get exceptional customer service.
3. We’re your Certificate Authority, literally.
4. Stronger brand identity.
Our premium certificates help increase user confidence by showing you’ve secured your true identity online after being validated by an industry-recognized Certificate Authority. So, your SSL certificate indicates to customers that your organization is committed to protecting their data and online experience.
5. “Not Secure.” Not good.
6. Increased SEO ranking.
Search engines heavily favor https-encrypted websites and will push them higher in search results. That vastly increases the likelihood customers will find you.
7. Compliance with regulation standards.
When you buy an SSL certificate, it provides the strongest protection for online businesses, including standards and regulations such as PCI-DSS, HIPAA, HITECH, GDPR and more.
8. Customers will trust you.
And that’s important because trust is the cornerstone of SSL protocol – indicative of strict validation guidelines. Our SSL certificates protect sensitive customer data on your site.
9.Safe mobile and online payment systems.
Give customers the payment options they prefer – and keep them shopping through checkout. To do that safely and securely you’ll need an SSL certificate, the industry standard for end-to-end encryption protocol to thwart hackers from getting to your sensitive data.
What is the TLS Handshake ?
The TLS (Transport Layer Security) handshake is a process that occurs at the beginning of a secure communication session between a client and a server. It’s a crucial step in establishing a secure connection and involves several steps to ensure the confidentiality and integrity of the data being transmitted. The TLS handshake generally follows these key steps:
- ClientHello:
- The client initiates the handshake by sending a “ClientHello” message to the server. This message includes information such as the highest TLS version the client supports, a list of supported cryptographic algorithms, and other parameters.
- ServerHello:
- The server responds with a “ServerHello” message. This message includes information such as the chosen TLS version, the selected cryptographic algorithms, and other parameters. It also typically contains the server’s digital certificate.
- Authentication and Key Exchange:
- The server’s digital certificate is sent to the client. The client verifies the authenticity of the certificate by checking its digital signature and ensuring it’s signed by a trusted certificate authority (CA).
- If the authentication is successful, the client generates a pre-master secret and encrypts it with the server’s public key (from the server’s certificate). This encrypted pre-master secret is sent back to the server.
- Session Key Generation:
- Both the client and server independently derive the session key from the pre-master secret. This process usually involves additional random values exchanged during the handshake.
- The session key is used for symmetric encryption, providing a shared secret for encrypting and decrypting the data during the session.
- Finished:
- Both the client and server send “Finished” messages to each other, confirming that the handshake is complete. These messages are encrypted and include a hash of all the exchanged handshake messages, ensuring the integrity of the handshake.
- Secure Data Transfer:
- With the handshake completed successfully, the client and server can now use the established session key for secure data transfer. This involves symmetric encryption, where both parties use the same key for encryption and decryption.
The TLS handshake ensures that the client and server agree on a set of cryptographic parameters, authenticate each other, and establish a secure communication channel. The exchanged keys and parameters are used to encrypt and decrypt the data during the session, providing confidentiality and integrity for the transmitted information.
What is Symmetric Encryption of SSL ?
Symmetric encryption is a type of encryption where the same key is used for both the encryption of plaintext (original data) and the decryption of ciphertext (encrypted data). In the context of SSL/TLS (Secure Sockets Layer/Transport Layer Security), symmetric encryption is employed after the initial key exchange during the handshake process.
Here’s how symmetric encryption works in the context of SSL/TLS:
- Key Exchange:
- During the SSL/TLS handshake, a process called key exchange takes place. The client and server agree on a shared secret, often referred to as a “pre-master secret” or “session key.” This key is established using asymmetric encryption, where the server’s public key (from its digital certificate) is used to encrypt the secret, and only the server’s private key can decrypt it.
- Symmetric Key Derivation:
- Both the client and server independently derive the actual symmetric encryption key, often referred to as the “master secret,” from the pre-master secret. This derivation typically involves additional random values exchanged during the handshake.
- Symmetric Encryption:
- Once the master secret is established, both the client and server use it to derive encryption keys and initialization vectors for the symmetric encryption algorithm they’ve agreed upon (e.g., AES – Advanced Encryption Standard). The keys are used for both encryption and decryption of the data.
- Data Transfer:
- With the symmetric encryption keys in place, the client and server can now securely exchange data. The same key is used to encrypt the data on one end and decrypt it on the other, ensuring that only the entities with knowledge of the shared key can access the original data.
Symmetric encryption is faster and computationally less intensive than asymmetric encryption. However, one challenge is securely exchanging the initial key (pre-master secret) without interception. This is why the asymmetric encryption process is used during the handshake phase. Once the secure channel is established, symmetric encryption takes over for the actual data transfer, providing a balance of efficiency and security in the SSL/TLS protocol.
What is the Difference Between HTTP and HTTPS?
HTTP (Hypertext Transfer Protocol) and HTTPS (Hypertext Transfer Protocol Secure) are both protocols used for transmitting data over the internet, but they operate with different levels of security.
- HTTP (Hypertext Transfer Protocol):
- HTTP is the standard protocol for transmitting data over the internet. It is the foundation of any data exchange on the web and is commonly used for accessing and transmitting hypertext content. However, HTTP does not provide a secure connection, meaning that the data transferred between the user’s browser and the web server is not encrypted.
- HTTPS (Hypertext Transfer Protocol Secure):
- HTTPS is the secure version of HTTP. It uses a combination of HTTP and a security protocol called SSL/TLS (Secure Sockets Layer/Transport Layer Security) to encrypt the data exchanged between the user’s browser and the web server. This encryption helps protect sensitive information, such as login credentials, credit card numbers, and other personal data, from being intercepted by malicious actors.
Key Differences:
- Encryption:
- The primary difference between HTTP and HTTPS is the level of security provided. HTTP does not encrypt the data transmitted between the client (user’s browser) and the server, making it susceptible to eavesdropping and tampering. In contrast, HTTPS encrypts the data, ensuring that even if intercepted, it cannot be easily deciphered.
- Protocol:
- HTTP uses a plain text protocol, while HTTPS uses a secure version of the same protocol. The “S” in HTTPS stands for “Secure,” indicating the use of encryption to protect data in transit.
- Port Number:
- HTTP typically operates on port 80, while HTTPS operates on port 443. This is a default convention, and web servers can be configured to use different ports, but these are the standard port numbers.
- URL Scheme:
- In a web browser, URLs for HTTP connections begin with “http://” (e.g., http://www.powerhoster.com), while URLs for HTTPS connections begin with “https://” (e.g., https://www.powerhoster.com). This visual indicator helps users know whether they are accessing a secure site.
In summary, the main difference between HTTP and HTTPS is the security aspect. HTTPS provides a secure and encrypted connection, making it the preferred choice for websites that handle sensitive information. As a best practice, websites that collect user data or involve transactions should use HTTPS to protect the privacy and security of users.
What is SSL Certificate ?
SSL stands for Secure Sockets Layer, a global standard security technology that enables encrypted communication between a web browser and a web server. It is utilized by millions1 of online businesses and individuals to decrease the risk of sensitive information (e.g., credit card numbers, usernames, passwords, emails, etc.) from being stolen or tampered with by hackers and identity thieves. In essence, SSL allows for a private “conversation” just between the two intended parties.
To create this secure connection, an SSL certificate (also referred to as a “digital certificate”) is installed on a web server and serves two functions:
- It authenticates the identity of the website (this guarantees visitors that they’re not on a bogus site)
- It encrypts the data that’s being transmitted
Are all SSL Certificates the Same ?
No.
There are many different types of SSL certificates based on the number of domain names or subdomains owned, such as:
- Single – secures one fully-qualified domain name or subdomain name
- Wildcard – covers one domain name and an unlimited number of its subdomains
- Multi-Domain – secures multiple domain names
and the level of validation needed, such as:
- Domain Validation – this level is the least expensive, and covers basic encryption and verification of the ownership of the domain name registration. This type of certificate usually takes a few minutes to several hours to receive.
- Organization Validation – in addition to basic encryption and verification of ownership of the domain name registration, certain details of the owner (e.g., name and address) are authenticated. This type of certificate usually takes a few hours to several days to receive.
- Extended Validation (EV) – this provides the highest degree of security because of the thorough examination that is conducted before this certificate is issued (and as strictly specified in guidelines set by the SSL certification industry’s governing consortium). In addition to ownership of the domain name registration and entity authentication, the legal, physical and operational existence of the entity is verified. This type of certificate usually takes a few days to several weeks to receive.
Who may need an SSL certificate?
Any individual or organization that uses their website to require, receive, process, collect, store, or display confidential or sensitive information. Some examples of this information are:
- logins and passwords
- financial information (e.g., credit card numbers, bank accounts)
- personal data (e.g., names, addresses, social security numbers, birth dates)
- proprietary information
- legal documents and contracts
- client lists
- medical records
Where can you get SSL certificates?
Probably the most important part of an SSL certificate is where it comes from. SSL certificates are issued by Certificate Authorities (CAs), organizations that are trusted to verify the identity and legitimacy of any entity requesting a certificate.
The CA’s role is to accept certificate applications, authenticate applications, issue certificates, and maintain status information on certificates issued.
You may also be able to purchase digital certificates from a domain name registrar or website hosting provider.
How will visitors know my site has an SSL certificate?
There are four visual clues:
- Padlock to the left of a URL
- https URL prefix instead of http
- A trust seal
- A green address bar (when an EV SSL certificate is issued
